Everything began in the summer of 2017...a lonely IoT camera was getting dusty on my table, I remember I bought it back in 2016 to check what's going on at home when I'm on vacation but I guess that was just a bad justification to get a new toy.
Actually I don't like surveillance cameras, we already have a lot of them to fight crime & terrorism but often they don't help at all. They don't prevent crime, the only thing they might do is moving crime to another place. Unfortunately the recent news about increasing home burglaries lead to a spike of private surveillance. So what's the problem here?
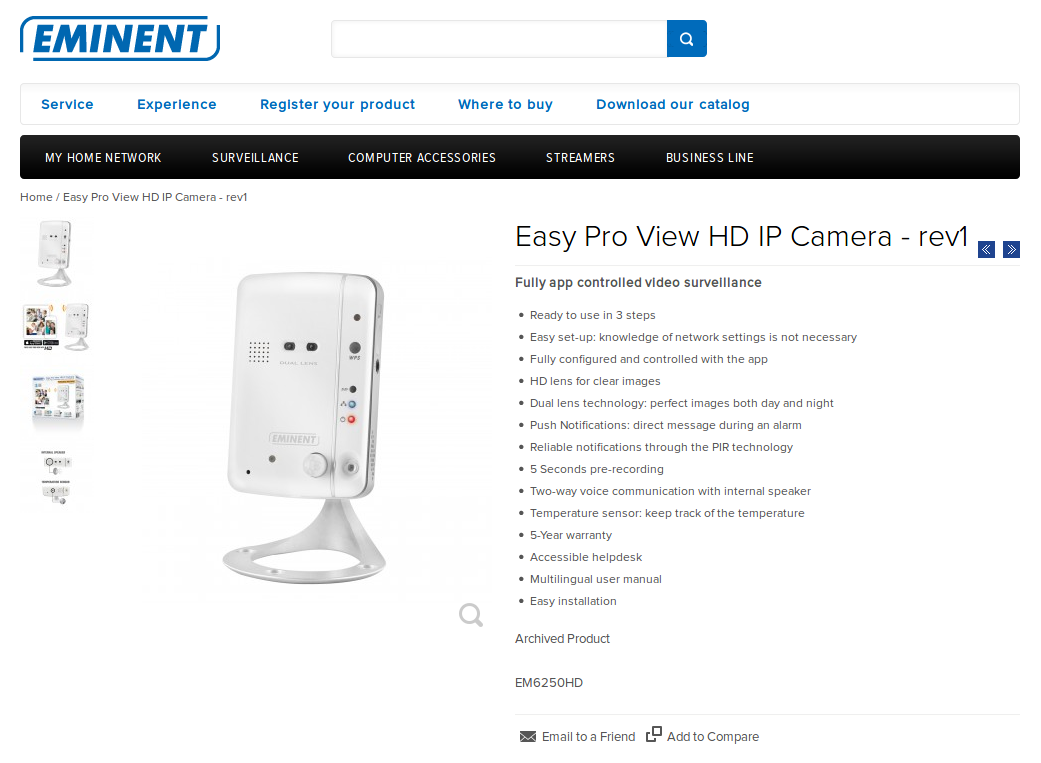
People buy "smart" surveillance gear to "protect" their homes, they set up indoor & outdoor cameras and connect them to their home networks.
That's how such a thing looks like:
Source: https://goo.gl/46gsF8
It doesn't look that scary, does it? Well, it depends... ;-) It has a microphone, two HD lenses for day and night view, a passive infrared sensor (PIR), a speaker and it supports WiFi/Ethernet. Furthermore you can insert a SD card to save recorded videos. You can still buy it online if you like but after reading this I guess you won't.
https://www.amazon.de/Eminent-EM6250HD-Wireless-IP-Cam/dp/B00I5HGAIG
It also has some nice hidden features, it's completely broken from a security aspect:
- count(XSSs & CSRFs) → ∞
- backdoor account (supervisor:dangerous)
- command injections as uid=0
- no auto-update (not sure if that's good or bad...at least they didn't go the auto RCE way aka 'loading unsigned binaries via HTTP')
If you combine it all you end up with a nice unauthenticated remote code execution as root. Let's put it together:
The camera uses basic access authentication to restrict access to the administration panel but inside the firmware there's a hidden backdoor account. It's called supervisor with the password dangerous, they knew what they were doing but they did it anyway.
My exploit uses the hard-coded backdoor account to send an authenticated POST request exploiting a command injection flaw to /cgi-bin/wlanset.cgi. The payload will start the telnet server to enable remote shell access. If the camera is connected via WiFi you'll lose the connection, better use the second command injection flaw on /cgi-bin/smtpset.cgi.
Quick demo:
That's awesome but boring...not everybody enables port forwarding, you miss a lot of vulnerable devices. Inspired by SkyLined's LocalNetworkScanner I did some research and found Mathew Ulm's js-recon.html. I modified it and added image based fingerprinting, here's a short demo:
Now we've a weaponized & reliable remote code execution exploit for the device, but we can even hit devices inside home networks. A simple website visit would be enough to get your device compromised. But it's limited to a single Eminent device? Nope, I found a lot of affected devices from multiple vendors:
Accessing those devices without authorization would harm the privacy of their owners, in addition it would be a criminal offense in Germany. That's why my list is likely incomplete, sometimes model information isn't publicly accessible information.
The main problem for the average user is you can only trash the devices to stay safe, only StarVedia fixed the vulnerabilities. I would recommend to create a seperate network for all IoT devices you have...or make those smart devices dumb again!
Using such a device allows anybody to spy on you, your family and friends. Watching you eat, sleep or having fun...everything could be recorded including sound, temperature & moves. Wouldn't you pay for certain videos to stay offline? You make yourself susceptible to blackmail. That's not even all, the same device that should protect your home will happily betray you and tell criminals when you're usually leaving the house.
All companies using those devices should immediately disconnect them or they will be used for corporate espionage or as a network entry for WannaCry 2.0.
I worked together with Beyond Security to coordinate the responsible disclosure process.
Exploits: